How iTivity Works
iTivity iAgents isolate vendor systems from the rest of the network and tunnel all traffic through the iSAT (iTivity Secure Access Tunnel).
The iSAT (iTivity Secure Access Tunnel) uses 2048 bit RSA asymmetric key exchange and AES encryption with 256 bit bulk/session/symmetric keys.
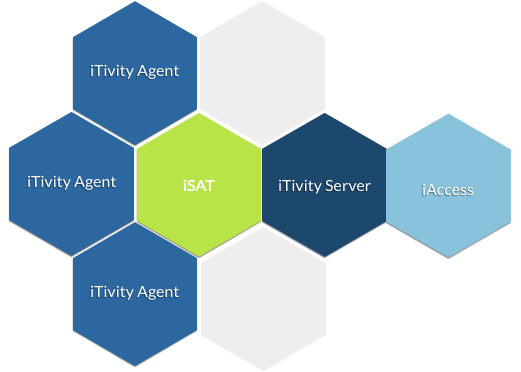
The iTivity iServer forms the hub of the iTivity Virtual Secure Network. The iServer creates and coordinates secure connections to iAgents and iAccess users.
iManager connects authorized users to the iServer and provides a single point of access to all systems available to a user.
Learn more.
Download the whitepaper, “Quarantined: How iTivity Works,” and learn how easily and effectively iTivity can secure every vendor system on your network.

