|
8. Installing and Running the Unattended iAgent on Linux or UNIX
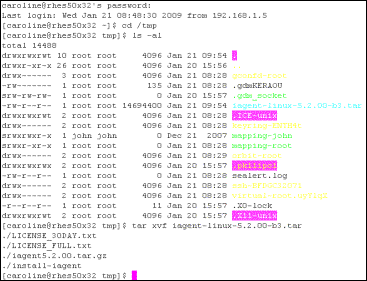
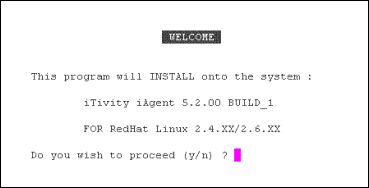
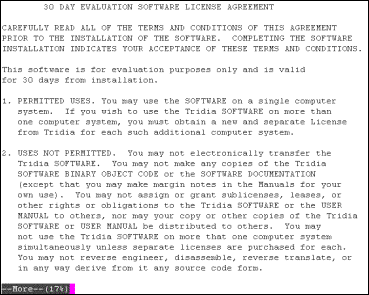
iTivity provides a UNIX/Linux version of the Unattended iAgent for remote support of UNIX/Linux systems. This chapter explains how to install, configure and use the Unattended iAgent on UNIX or Linux. 8.1 Capabilities of the Unattended iAgent on
|
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
COMMON OPTIONS |
|
|
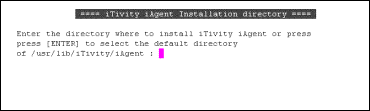
Programdir |
Specifies the directory in which the Unattended iAgent is installed. This setting is automatically configured by the Installation program. Default: /usr/lib/iTivity/iAgent |
|
dataDir |
Specifies the directory where the Unattended iAgent stores information between program invocations. This information includes encryption keys and other data used internally. Default: /usr/lib/iTivity/iAgent/itivity_data |
|
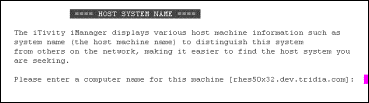
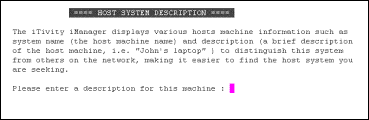
vnchostname vnchostdesc |
The iAgent name and Description as listed in iTivity iManager for this Unattended iAgent. The default vnchostname is the UNIX/Linux machine name. The vnchostdesc can be entered during the Installation procedure. |
|
CONNECTOR |
|
|
randomFile keyFile caFile |
These settings specify the filenames and location of three files used for encryption. The Unattended iAgent automatically generates default versions of these files the first time it runs. There is no need to change these settings unless the default files in the dataDir directory are not acceptable. Defaults: randomFile=/usr/lib/iTivity/IAgent/itivity_data/random.dat keyFile=/usr/lib/iTivity/iAgent/itivity_data/keys.pem caFile=/usr/lib/iTivity/iAgent/itivity_data/root.pem |
|
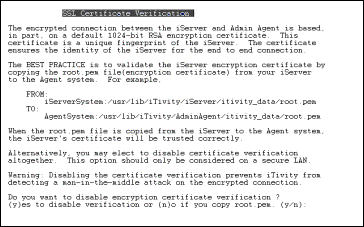
autoAcceptAllCerts |
This flag enables or disables verification of the encryption certificate received from the iServer. Enabling this option (setting the value = 1) prevents a change in the encryption certificate on the iServer from blocking access. Caution: Enabling this function prevents iTivity from detecting a man-in-the-middle attack on the encrypted connection. The recommended practice is to copy the "root.pem" file from your iServer to the iAgent system. For example, From: To: When the root.pem file is copied from the iServer to the iAgent system the iServer's certificate will be trusted correctly. At this point, autoAcceptAllCerts can remain disabled and providing a higher level of security. Default: autoAcceptAllCerts=0 |
|
Log File Flags |
The following options control which events are written to the Syslog. A value of 1 (one) enables logging and a value of 0 (zero) disables logging. Syslog facility and priority: iTivity.daemon |
|
connectSysLogMask |
Arrival of an encrypted connection. Default = 0. |
|
disconnSysLogMask |
Closing of an encrypted connection. Default = 0. |
|
startSysLogMask |
iAgent startup. Default = 1. |
|
stopSysLogMask |
iAgent shutdown. Default = 1. |
|
allowSysLogMask |
Granting of user permission by the iAgent. Default = 0 |
|
sshServiceSysLogMask |
Initiation of an SSH session with the iAgent. Default = 0 |
|
telnetServiceSysLogMask |
Initiation of a TELNET session with the iAgent. Default = 0 |
|
ftpServiceSysLogMask |
Granting of FTP access by the iAgent. Default = 0 |
|
chatServiceSysLogMask |
Granting of Chat access by the iAgent. Default = 0 |
|
termRCServiceSysLogMask |
Granting of terminal remote control at the iAgent via DoubleVision Pro. Default = 0 |
|
TCP Connection |
These settings control the TCP connection ports and interface of the Unattended iAgent. |
|
transportPort |
Must always match proxySvcPort=21800. Default = 21800 |
|
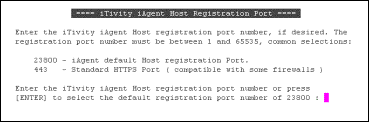
iasServerPort |
The port for iServer connections. Default = 23800. |
|
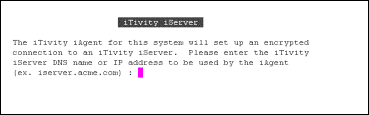
iasServerHost |
Host DNS for the iServer. Note: You must enter the DNS name for your iServer here for the iAgent to connect. Default none. Example: iserver.acme_heavy_industries.com |
|
transportTimeout serviceTimeout |
These two settings control the timeout behavior of Unattended iAgent data connections. transportTimeout - Timeout in milliseconds set for end-to-end or host to host network connections. Keep this value high if using the Internet or other high-latency network transport (such as satellite connections). serviceTimeout - Timeout in milliseconds for internal or local connections between Unattended iAgent daemons. Defaults: transportTimeout=90000 serviceTimeout=45000 |
|
Keep-Alive Settings |
These three settings control the keep-alive behavior of Unattended iAgent data connections. |
|
endToEndKeepAlive |
Determines whether the Unattended iAgent sends keep alive packets. Not supported on all transports. Values are: 1 (one) - send packets Default = 1. |
|
iasVerifySessionFlag |
In addition, the Unattended iAgent can send application messages to guarantee the connections are viable and detect lost connections more reliably. Set this flag to 1 (enabled) to have the iServer verify session status when there is otherwise no network traffic. Values are 1, enabled, and 0, disabled. Default = 1. |
|
iasVerifySessionTimeout |
If the iasVerifySessionFlag is set to 1, this value controls how often, in seconds, the verification packets are sent. Default = 240. |
|
connectToIASCycleTime connectToIASIntervalRetries connectToIASMaxRetries |
These settings control the reconnect behavior of the Unattended iAgent when the connection to the iServer fails. The default is to retry every five minutes for 24 hours and then enter a binary-backoff retry timing. During the binary-back off stage the retry interval is doubled for each failed connection attempt. connectToIASCycleTime is the cycle time specified in milliseconds between reconnect tries during the first stage of equal intervals. Default = 300000. connectToIASIntervalRetries is the total number of equal interval retries. Default = 288. The default works out to about 24 hours if the cycle time above is also at default. connectToIASMaxRetries is the maximum number of retries of any kind. Assign this setting a value of -1 to allow unlimited retries. Default = -1. |
|
disableSessionDNSLookup |
Prevents DNS lookups for new connections to query the host name of the foreign system. This can be useful to improve performance in environments with slow DNS service. Values are: 1 (one) - prevent DNS lookup Default = 0. |
|
cipherList |
Specifies the list of cipher algorithms to be allowed for incoming connections. If you add other ciphers to the list, it is highly recommended that you keep the default setting as an option. If this Unattended iAgent connects to an iServer or is contacted by an iManager and there is no mutually acceptable cipher algorithm, the connection will fail. In order for a different cipher to be used, it must also be allowed by the cipherList of the iServer. The recommended best practice is to set the same cipherList in all iTivity systems. Supported OpenSSL ciphers: DHE-RSA-AES256-SHA:DHE-DSS-AES256-SHA AES256-SHA Default: cipherList= AES128-SHA:DES-CBC3-SHA |
|
Connector Port Number |
These settings provide the ability to control the port number on which the Connector will attempt to find the local service daemons. Local service daemons listen on the localhost interface and provide local, unencrypted access to services. |
|
|
commandSvcPort |
Remote control authorization and commands. Must always match connectPort=6800 Default = 6800 |
|
|
rfbSvcPort |
Unencrypted, raw VNC data Default = 5900 |
|
|
telnetSvcPort |
Telnet daemon Default = 23 |
|
|
ftpCtlSvcPort |
FTP server control port. Default = 21 |
|
|
ftpDataSvcPort |
FTP server data port (passive mode) Default = 20 |
|
|
proxySvcPort |
Forwarded iServer connections. Must always match transportPort=21800 Default = 21800 |
|
|
defaultHostPermissions |
This setting provides control over which services the iTivity iManager user can access on this iAgent system via iTivity. Each individual service is controlled via a bit flag in this integer. (See the Examples below.) The iManager user must first authenticate with the iAgent system before being allowed to access any services. After authentication (and the authorization check), then the remote user is subject to the permissions restrictions listed in the table. A Status of N/A indicates that this service is Not Available in the UNIX/Linux Unattended iAgent. Decimal 1 required Command Protocol 2 optional View desktop permission 4 N/A Control desktop permission 8 optional Telnet permission 16 optional FTP permission 32 required Proxy permission 64 N/A Chat permission 128 optional TTY remote control permission 256 optional TTY listing permission 512 N/A RDP permission 1024 N/A desktop sharing 2048 optional dynamic tunnel permission 4096 optional SSH permission The default is to allow access to all supported iTivity services (after remote user authenticates and passes authorization check). Default= 65535 Examples For FTP access only, use a value of 1 + 16 = 17, since the command protocol is required and the FTP permission has a value of 16. For telnet access only, use a value of 1 + 8 = 9. For TTY Listing and TTY remote control only, use a value of 1 + 128 + 256 = 385 |
|
|
PROXY SERVER |
These settings can be used configure the Unattended iAgent to connect to the iServer through a proxy server running the HTTP or SOCKS v5 protocol. |
|
|
socksMode |
One of the following iTivity modes used to define when the iAgent uses a Proxy Server to connect: 1 - Disable. Only connect to iServer directly, no proxy server used. 2 - Require. Only connect to iServer via proxy, no direct connect. 3 - Fallback. If direct connection fails, then attempt the proxy connection. 4 - Override. If the proxy connection fails, then attempt the direct connection. |
|
|
socksHost |
DNS name of the Proxy Server |
|
|
socksPort |
Port used to connect to the Proxy Server |
|
|
socksUser |
User name used for secure login to the Proxy Server. |
|
|
socksPwd |
Password used for secure login to the Proxy Server. |
|
|
hProxyMode |
One of the following iTivity modes used to define when the iAgent uses a Proxy Server to connect: 1 - Disable. Only connect to iServer directly, no proxy server used. 2 - Require. Only connect to iServer via proxy, no direct connect. 3 - Fallback. If direct connection fails, then attempt the proxy connection. 4 - Override. If the proxy connection fails, then attempt the direct connection. |
|
|
hProxyHost |
DNS name of the Proxy Server |
|
|
hProxyPort |
Port used to connect to the Proxy Server |
|
|
hProxyUser |
User name used for secure login to the Proxy Server. |
|
|
hProxyPwd |
Password used for secure login to the Proxy Server. |
|
|
debugMode |
Enables debugging output in the connector daemons. A setting of zero ("0") disables output. As the mode number increases from one ("1") to twelve ("12"), more and more information is written to the log file. This option should be disabled in production systems, unless instructed otherwise by Tridia staff. Default = 0. |
|
|
PROCESSOR |
|
|
|
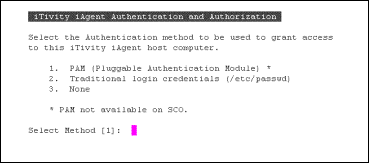
permissionGroup authscheme |
These settings control the authentication required of iTivity iManager users to view and control the Unattended iAgent system. The authscheme setting controls the way the Unattended iAgent authenticates. The default setting is “passwd”, which requires that the remote user have an account in the native /etc/passwd database. The other currently valid setting is "none, which disables authentication at the Unattended iAgent level may be disabled using the “none” setting. This is useful in environments where the iTivity iServer is trusted and its authentication is deemed sufficient. Other authscheme values are reserved for future use. The permissionGroup specifies the name of the user group with permission to view and access this system via the Unattended iAgent. To grant a user of iTivity iManager access, simply add the user to this group. To block a user from using the iServer, remove their user id from the group. A user in this group must log in with username and password before viewing this system through iTivity iManager. Defaults: |
|
|
logonSysLogMask logoffSysLogMask |
These flags control whether it is recorded in the syslog each time a user of iTivity iManager logs on and logs off of the iAgent system. Setting the flags to 1 (one) enables logging and provides an audit log of authentication. Setting the flags to 0 (zero) disables logging. Syslog facility and priority: iTivity.authpriv logonSysLogMask - Log iTivity iManager user logon (succeed or fail). Default = 1. logoffSysLogMask - Log iManager user logoff (disconnect). Default = 1. |
|
connectPort connectHost connectTimeout |
These settings specify the TCP network interface and port on which the processor daemon listens for new Unattended iAgent authentication connections. These connections are internal to the Unattended iAgent and generally use localhost. The connectPort value must always match the value of commandSvcPort. The connectTimeout value specifies the socket timeout for processor connections in milliseconds. Caution: Tridia strongly recommends that you do not change these settings. Defaults: |
|
supportDomain |
A comma separated list of support domain names which are authorized to access this iAgent system. See the iTivity Deployment Guide, Section 1.3, Advanced Authentication Using Permission Groups and Support Domains for more information. |
|
allowRemoteSettings |
This flag indicates whether iManager users are allowed to update the iAgent settings remotely (via the iManager user interface). Default: 1 (enabled) |
|
debugMode |
Enables debugging output in the processor daemon. The default setting of 0 (zero) disables output. As the number increases from 1 to 12, more and more information is written to the log file. This option should be disabled unless instructed otherwise by Tridia staff. Default: 0 (disabled) |
|
ITIVITY WEBTUNNEL SETTINGS |
These settings can be used to configure network applications that will be added to the iTivity WebTunnel scan list for this iAgent. For more information on WebTurnnel, see Section 1.5.1, Configuring iTivity WebTunnel. |
|
customAppScan_X |
Declares services or applications local to the iAgent that will be scanned by the iAgent for the purpose of application tunneling using iTivity WebTunnel. You can configure custom TCP network based services or applications specific to your environment. customAppScan definitions are indexed using a sequential number ordering. You can configure multiple applications as long as you increment the count. Example: customAppScan_1, customAppScan_2,… Tunneling of a custom application can be disabled by commenting out the service or application customScanApp_X definition in the iAgent.conf file and re-loading the iAgent configuration settings. |
|
port |
Declares the TCP port number of the local iAgent service or application. If the iAgent detects a daemon or service listening on your custom port, it will report the service or application as accessible to a connected iManager. The port value should be between 0 and 65536. This is a required setting for an enabled customAppScan definition. |
|
protocol |
Declares the protocol used by the local iAgent service or application. Supported protocols include: http, https, telnet, vnc, rdp For web applications, the protocol should be either “http” or “https’. This is a required setting for an enabled customAppScan definition |
|
appname |
Declares the user readable display name of the service or application to be tunneled. The name should have a clear meaning to an iManager user. This setting is not required but is highly recommended. |
|
session |
Some operating systems have platform specific session labels. This setting should declare the session in which the application or service is running, if any. Typical session names would include “tty0”,”pts/4”,’:4”k”tcp”,”#7’, etc. This setting is optional. |
|
path |
Specifies the path to the default page or landing page for the application. Typically used for web/http applications. This configuration setting is optional. |
8.4.2 Changing a Configuration
You can change configuration options without stopping and restarting the Unattended iAgent software. The options can be changed without losing current connections.
To reload the settings of a running Unattended iAgent, run the following script:
/usr/lib/iTivity/iAgent/iagent_config_reload
8.5 UNIX/Linux Unattended iAgent Commands
Administrators can use the programs explained in this section to display information about the Unattended iAgent and control its operation. These commands can be found in the iAgent installation directory. By default, the iAgent installation directory is:
/usr/lib/iTivity/iAgent/
iagent_downall
This command stops execution of the Unattended iAgent by stopping all daemons.
iagent_version
This command displays version information for the currently installed Unattended iAgent.
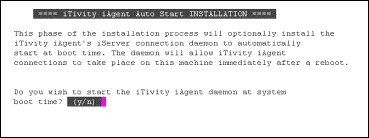
install_daemon
This command installs the scripts that launch the Unattended iAgent at boot time.
rc_iagent_daemon
This script starts the Unattended iAgent at system startup.
remove-iagent
This program removes the Unattended iAgent files from the system.
start_iagent
This program can be used to manually start the Unattended iAgent.
stop_iagent
This program can be used to manually stop the Unattended iAgent.
![]()
| Table of Contents |
Copyright © 2017 - 2023, iTivity Corporation
Copyright © 2004 - 2016, Tridia Corporation
Copyright and License Information